
What’s Firewall?
The firewall’s is A community safety programs. The Firewall’s monitor and controled each incoming & outgoing networks site visitors based mostly on the safety rule’s. firewall set up the barrier between each trusted inner community and un-trusted exterior community, as Web.essential objective of firewall is to separate a safe Connection space from a much less safe space and management the communication between the two space connection.
A firewall additionally management’s the inbound & outbound communications of something from the certainly one of machine to your entire networks.
A firewall generally is a combos of the {hardware} and software program or each.
The Firewalls are sometimes utilizing to prevented the unauthorized Web person’s from the accessing personal community’s related to the Web. The All packets of information that enter or exit an intranet go via a firewall are checked & blocks of that don’t meet the safety criterion’s are blocked.
firewall are configured to guard towards the unauthorized login from the surface world. This assist to stop hacker from getting into the machine of your networks.firewall block the exterior site visitors , however firewall permits person inside to the talk extra simply from exterior.
Benefits of firewall:
1) displays site visitors:
To The firewalls monitor’s all of the site visitors getting into your pc networks. A two-way the firewalls does double obligation & additionally it is monitor’s the site visitors going out of the networks.
The Info’s is shipped within the packet’s over the networks. The firewalls checked these the packet’s & determined if there may be something doubtlessly harmful in it.
2) blocks Trojans:
firewall assist in blocking Trojan horses. it sticks to the information in your pc, and while you ship that file, they harm to the vacation spot.
Trojans are harmful as a result of they transmitted silently . You might be unaware of Trojans presence till unusual issues occur to your pc.
Trojans infect your pc , however earlier than infecting a firewall can cease Trojans.
3) Prevents Hackers:
firewall at all times hold hackers out of your community. hackers can simply hack your pc or unfold viruses With out firewall safety.
4) firewall protects unauthorized distant entry
the worst issues occur in your pc is distant entry to your community / pc by unauthorized hackers. Firewalls stop all unauthorized distant entry to your pc.
Historical past of Firewalls
First Era: Packet Filter
first community firewall is known as a packet filter. The packet filter community deal with and port the packet which checks whether or not they need to dropped or permit or rejected.
So That The primary paper on the firewalls know-how was printed in 1988, when the engineers on the Digital Tools Company (DEC) developed by filter system referred to as the packet filtration firewalls.
packet filter could be very primary system through which the options of technical web safety have been added later.
Packet filters work by inspecting packets being switch between computer systems on the Web. When packet would not match the set of packets filter rule, that packet filter is both dropped or the packet is rejected.
it permits it to go , when a packet matches one program or extra program filter guidelines.
packet filters embody packet vacation spot deal with , ports of supply and vacation spot , and supply and protocol.
Second Era: “Stateful” Filters
In This 1989–1990, Three companion’s of AT&T Bell Laboratories, Dave Presto, Janardan Sharma & Horizon Companies, developed the second technology of firewall’s, known as circuit-layer gateway’s.
The Second-generation firewall’s perform’s like their first-generation ancestors however as much as layer 4 (transport layer) of the OSI Fashions.
So On this the packet is retained till adequate data’s is on the market to determine it’s standing.
So To The Know as The statefet packet’s inspection’s, it’s document’s all of the connection’s passing via the decide’s whether or not the packet’s is the start of the brand new connection’s, a components of an current connection’s, or components of any connection’s Shouldn’t be.
So Though static rule’s are the nonetheless used, connection rule’s are actually includeding in these rule’s.
Third Era: Software Layer
So That The Marcus Ranam, Wei Xu, & Peter Churchiard developed the applying firewall’s, referred to as the Firewall’s Toolkit (FW TK).
So In June 1994, Wei Ju prolonged to the FWTK to an IP deal with filtration and socket. So It was beforehand launched because the industrial merchandise of the Gauntlet firewalls of the Clear Software Firewalls. To The Gauntlet firewalls was one of many prime most firewalls throughout In 1995–1998.
To The main advantages of filtering utility firewall’s was that it may “understanding” sure The applying’s and protocol’s (similar to a File Switch Protocol (FTP), Area Title System (DNS), and Hypertext Switch Protocol (HTTP)).
So That is The very helpful as a result of it may well detect if an the spam functions or companies is attempting to the bypassing a firewall utilizing a protocol on a permitted port, and it may be detect that the protocol in any dangerous methods Being abused or not.
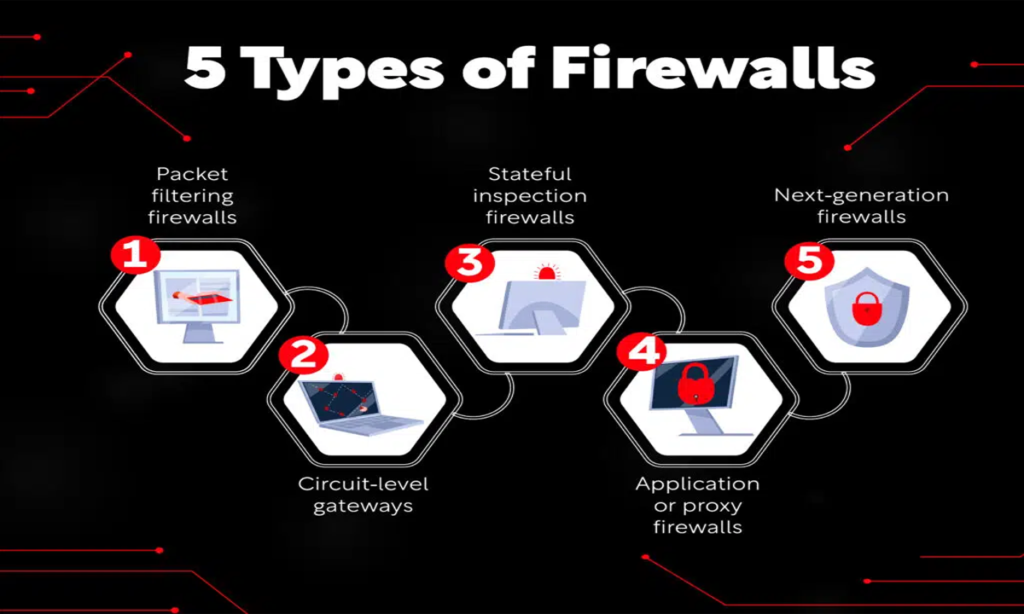
Kinds of Firewalls
1) Proxy firewall:
You Can See the earlier publish for the extra data’s about what a proxy servers or firewall’s is.
2) Stateful Inspection Firewall:
So Now regarded as the “conventional” firewalls, The Stateful Inspection Firewalls blocks or permit to the site visitors based mostly on the state, port, and protocols.
So It monitor’s all of the actions till the connections is closed after opening. So The filtration’s Of the choice’s are made based mostly on the each directors So To outline’s the rule’s and the context’s, Through which refer’s to the utilizing of the knowledge’s from the earlier connection’s and packet’s associated to the identical connections.
3) Unified Risk Administration (UTM) Firewall:
The Stateful Inspections in a UTM gadget usually join’s the firewalls to an intrusions prevention and antiviruses. This will additionally the together with further companies and cloud administration. So The principle focus of the UTM is on simplicity and ease of the use.
4) Subsequent-generation Firewall (NGFW):
In This firewalls has developed past the easy packets filtering and stateful inspections. The Most Of The businesses put in subsequent technology firewall’s to the stop from fashionable of malware and functions layer assault’s.
This materials was supplied by akdoogle.com/ solely for instructional/informational functions .Administrator shouldn’t be liable for its content material.Comply with us on social media/download app to remain updated with our software program updates!










